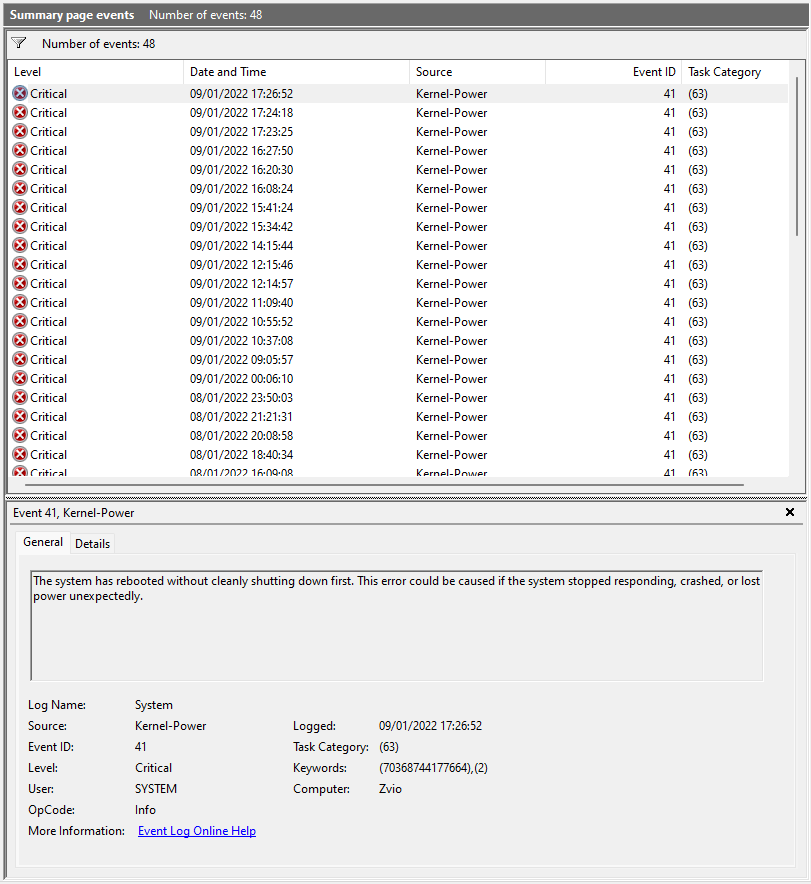
I tried many solutions I've found on the web but the error still occurs. I checked the event viewer and it says "Event 41, Kernel-Power (70368744177664),(2)".
PC Specs:
CPU: Ryzen 5 5600G
Mobo: MSI Mag B550m Bazooka
RAM: TForce Vulcan Z 3200 8GB 2x
SSD: Kingston SNVS/500GB
HDD 1: HGST HTS545050A7E680
HDD 2: TOSHIBA MK2555GSX
PSU: SilverStone ST70F-ES230
WinDBG Preview:
Microsoft (R) Windows Debugger Version 10.0.22473.1005 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\MEMORY.DMP]
Kernel Bitmap Dump File: Kernel address space is available, User address space may not be available.
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 19041 MP (12 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Edition build lab: 19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Kernel base = 0xfffff803
Debug session time: Sun Dec 26 01:17:09.494 2021 (UTC + 8:00)
System Uptime: 0 days 0:02:41.094
Loading Kernel Symbols
...............................................................
................................................................
..............Page 370a96 not present in the dump file. Type ".hh dbgerr004" for details
...................................
Loading User Symbols
PEB is paged out (Peb.Ldr = 00000000
SYMBOL_NAME: nt!KeAccumulateTicks+2061be
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
STACK_COMMAND: .cxr; .ecxr ; kb
BUCKET_ID_FUNC_OFFSET: 2061be
FAILURE_BUCKET_ID: CLOCK_WATCHDOG_TIMEOUT_INVALID_CONTEXT_nt!KeAccumulateTicks
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {95498f51-33a9-903b-59e5-d236937d8ecf}
Followup: MachineOwner
---------
Link for the dmp file: https://www.dropbox.com/s/2rav5wijbj8qky1/MEMORY.DMP?dl=0
Event Viewer Screenshots:
https://www.dropbox.com/s/soalyufurx75x0v/Screenshot 2022-01-09 174345.png?dl=0
PC Specs:
CPU: Ryzen 5 5600G
Mobo: MSI Mag B550m Bazooka
RAM: TForce Vulcan Z 3200 8GB 2x
SSD: Kingston SNVS/500GB
HDD 1: HGST HTS545050A7E680
HDD 2: TOSHIBA MK2555GSX
PSU: SilverStone ST70F-ES230
WinDBG Preview:
Microsoft (R) Windows Debugger Version 10.0.22473.1005 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\MEMORY.DMP]
Kernel Bitmap Dump File: Kernel address space is available, User address space may not be available.
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 19041 MP (12 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Edition build lab: 19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Kernel base = 0xfffff803
38a00000 PsLoadedModuleList = 0xfffff8033962a1b0Debug session time: Sun Dec 26 01:17:09.494 2021 (UTC + 8:00)
System Uptime: 0 days 0:02:41.094
Loading Kernel Symbols
...............................................................
................................................................
..............Page 370a96 not present in the dump file. Type ".hh dbgerr004" for details
...................................
Loading User Symbols
PEB is paged out (Peb.Ldr = 00000000
00361018). Type ".hh dbgerr001" for details
Loading unloaded module list
..........
For analysis of this file, run !analyze -v
nt!KeBugCheckEx:
fffff80338df70d0 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:ffffe081569dbc90=0000000000000101
3: kd> !analyze -v
*******************************************************************************
[LIST]
[*]*
[*]Bugcheck Analysis *
[*]*
[/LIST]
*******************************************************************************
CLOCK_WATCHDOG_TIMEOUT (101)
An expected clock interrupt was not received on a secondary processor in an
MP system within the allocated interval. This indicates that the specified
processor is hung and not processing interrupts.
Arguments:
Arg1: 0000000000000010, Clock interrupt time out interval in nominal clock ticks.
Arg2: 0000000000000000, 0.
Arg3: ffffe08156ed8180, The PRCB address of the hung processor.
Arg4: 000000000000000a, The index of the hung processor.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 1530
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 1662
Key : Analysis.Init.CPU.mSec
Value: 233
Key : Analysis.Init.Elapsed.mSec
Value: 5805
Key : Analysis.Memory.CommitPeak.Mb
Value: 73
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
FILE_IN_CAB: MEMORY.DMP
BUGCHECK_CODE: 101
BUGCHECK_P1: 10
BUGCHECK_P2: 0
BUGCHECK_P3: ffffe08156ed8180
BUGCHECK_P4: a
FAULTING_PROCESSOR: a
PROCESS_NAME: NoxVMHandle.exe
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
STACK_TEXT:
ffffe081569dbc88 fffff80338e1f36e : 0000000000000101 0000000000000010 0000000000000000 ffffe08156ed8180 : nt!KeBugCheckEx
ffffe081569dbc90 fffff80338c1c3cd : 0000000000000000 ffffe081569c2180 0000000000000246 0000000000002846 : nt!KeAccumulateTicks+0x2061be
ffffe081569dbcf0 fffff80338c1c971 : 000000000000282b 0000000000001801 ffffe081569c2180 0000000000000001 : nt!KiUpdateRunTime+0x5d
ffffe081569dbd40 fffff80338c167e3 : ffffe081569c2180 0000000000000000 fffff80339631588 0000000000000000 : nt!KiUpdateTime+0x4a1
ffffe081569dbe80 fffff80338c1f1a2 : ffffb10370e3eaf0 ffffb10370e3eb70 ffffb10370e3eb00 000000000000000c : nt!KeClockInterruptNotify+0x2e3
ffffe081569dbf30 fffff80338cde135 : 0000000060280997 ffffb403f44d3e60 ffffb403f44d3f10 ffff5b0972e2939b : nt!HalpTimerClockInterrupt+0xe2
ffffe081569dbf60 fffff80338df8b7a : ffffb10370e3eb70 ffffb403f44d3e60 0000000000000001 0000000000000000 : nt!KiCallInterruptServiceRoutine+0xa5
ffffe081569dbfb0 fffff80338df90e7 : 000000002c0d31a1 ffffe081569c5088 ffffb10370e3ec21 ffd881b871f66804 : nt!KiInterruptSubDispatchNoLockNoEtw+0xfa
ffffb10370e3eaf0 fffff80338c3a656 : 0000000000000000 0000000000000000 0000000000000002 fffff400066095d0 : nt!KiInterruptDispatchNoLockNoEtw+0x37
ffffb10370e3ec80 fffff80338c3a448 : fffff14f40728fe8 0000000000000000 fffff80339650b00 0000000000000000 : nt!KeFlushMultipleRangeTb+0x166
ffffb10370e3ed20 fffff80338cb2e1c : 0000000000000000 000000000000d0e0 fffff14f40728fd8 0000000000000000 : nt!MiFlushTbList+0x88
ffffb10370e3ed50 fffff80338cb5005 : ffffb10370e3f070 ffffb10370e3f080 ffffb10370e3ef80 fffff178a7a03940 : nt!MiFlushTbAsNeeded+0x11c
ffffb10370e3ee90 fffff80338c587aa : ffff9e80e51f9000 fffff10000000000 ffffb10370e3ef80 ffffb1030000000a : nt!MiLinkPoolCommitChain+0x65
ffffb10370e3eef0 fffff80338c58627 : 0000000000000000 0000000000001000 0000000000000001 0000000000000000 : nt!MiCommitPoolMemory+0xfe
ffffb10370e3ef40 fffff80338c58464 : 0000000000004000 ffffb10370e3f040 0000000000000000 ffff9e8000000004 : nt!MmAllocatePoolMemory+0xcf
ffffb10370e3f000 fffff80338c582b5 : ffff9e80e51f9000 ffffb10370e3f168 0000000000004000 0000000000000004 : nt!RtlpHpEnvAllocVA+0xc8
ffffb10370e3f070 fffff80338c57c15 : 0000000000000000 00000000000000c0 00000000000000e0 0000000000000000 : nt!RtlpHpAllocVA+0xf5
ffffb10370e3f130 fffff80338c579ae : 0000000000000000 0000000000000004 0000000000000000 0000000000000004 : nt!RtlpHpSegMgrCommit+0xf5
ffffb10370e3f200 fffff80338c56e0b : 0000000000000001 ffff9e80e5101f20 0000000000000000 ffffb40400000004 : nt!RtlpHpSegPageRangeCommit+0x1ee
ffffb10370e3f2a0 fffff80338c8d0a6 : 0000000000004000 0000000000004000 ffffb10370e3f3e1 0000000080000001 : nt!RtlpHpSegAlloc+0xab
ffffb10370e3f300 fffff80338c8c77f : ffff9e80dcae9cc0 0000000000000008 0000000074536d4d fffff80338ff787e : nt!ExAllocateHeapPool+0x8f6
ffffb10370e3f440 fffff80338c48006 : 0000000080000000 0000000000004000 0000000074536d4d fffff40000000000 : nt!ExpAllocatePoolWithTagFromNode+0x5f
ffffb10370e3f490 fffff80338c635bf : 0000000000000000 ffffb10370e3f550 0000000000000800 0000000000000000 : nt!MiAllocatePool+0x86
ffffb10370e3f4e0 fffff80338c49052 : ffffffffffffffff ffffffffffffffff ffffb403f9cfca30 ffffb40300000000 : nt!MiCreatePrototypePtes+0x53
ffffb10370e3f590 fffff80338ffd877 : ffffb40400000000 0000000000000800 ffffb10370e3f901 ffffb40300000800 : nt!MiAddViewsForSection+0x3c2
ffffb10370e3f690 fffff80338ffd35c : 0000000000000004 0000000000000000 ffffb10370e3f968 ffffb10370e3f978 : nt!MiMapViewOfDataSection+0x197
ffffb10370e3f7c0 fffff80338ffedc9 : 0000000000000021 ffffb10370e3fb40 000000001690ea10 0000000000000000 : nt!MiMapViewOfSection+0x34c
ffffb10370e3f910 fffff80338e08ab8 : ffffb40402504080 000000001690e928 0000000077566d4d 0000000000000021 : nt!NtMapViewOfSection+0x159
ffffb10370e3fa50 00007ff8fc7ed274 : 0000000000000000 0000000000000000 0000000000000000 0000000000000000 : nt!KiSystemServiceCopyEnd+0x28
000000001690e908 0000000000000000 : 0000000000000000 0000000000000000 0000000000000000 0000000000000000 : 0x00007ff8fc7ed274SYMBOL_NAME: nt!KeAccumulateTicks+2061be
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
STACK_COMMAND: .cxr; .ecxr ; kb
BUCKET_ID_FUNC_OFFSET: 2061be
FAILURE_BUCKET_ID: CLOCK_WATCHDOG_TIMEOUT_INVALID_CONTEXT_nt!KeAccumulateTicks
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {95498f51-33a9-903b-59e5-d236937d8ecf}
Followup: MachineOwner
---------
Link for the dmp file: https://www.dropbox.com/s/2rav5wijbj8qky1/MEMORY.DMP?dl=0
Event Viewer Screenshots:
https://www.dropbox.com/s/soalyufurx75x0v/Screenshot 2022-01-09 174345.png?dl=0


