In the current power draw and throttling situation, taking into account that the chips are good, it may be possible that we could get stable original clock with lower voltage. That would lead to a lower power draw, lower temperature and less ther7mal throttling. In turn, it may lead to a/ better performance. Hence, for many workloads, undervolting may reduce temperatures and power consumption and increase the performance... The plundervolt was due to causing instability in the processor, so setting the undervolting should require administrator's privileges but if the processor is fully stable, there is no vulnerability. Undervolting is als/o different than limiting the total power draw. To my knowledge, limiting the total power keeps the voltage curve unaltered, while undervolting affects the whole curve, hence for given power draw, we have more computing power.
Unfortunately, locking the CPUs to the default voltage curve via BIOS or firmware or microcode update or some other low level crap, pushed over Win update with a vague description and required install, was the way they went with mitigating Plundervolt. The conversation probably went something like "if someone is doing plundervolting maybe they kidnapped and tortured the admin and pwned everything." Something like that. iirc, this was before all the spectre/meltdown stuff came to lig/ht, so it was easier to cover up.
By the time Kaby Lake came around, Intel had an EXTREMELY optimized 14nm process due to years of screwing up the 10nm shrink, so I was able to drop the voltage curve on my 7th gen i7 laptop by -0.230v with no stability issues and huge benefits to cooling and the availability of turbo boost time. I couldn't even go over the PL1 limit with it running like that. One day it suddenly started overheating and a little research taught me all about this well thought out solution. My favorite part, event if I had made it unstable, the way Plundervolt worked meant that it never had any effect on my attack surface to begin with.
The mitigation itself was an attack that fixed something that wasn't broke. It felt analogous to being told my car is hard to see behind cause the mirror might be kinda iffy and ending up with a mandatory, legally enforced recall that installs a giant mirror that blocks 75% of the view out the front. Maybe there are people that can't turn around and drive their cars all out in reverse gear, but I'm not one of them.
I wish I knew how to undervolt for craptops. The problem is that I've never seen a craptop BIOS that allows that level of customisation. All of the ones I've owned w8ere more or less locked into an "as-is" mode.
I used a techpowerup program called throttlestop. It let you adjust voltage curves in real time for CPU core, ring bus, IMC, GPU, and an uncore or something. Even though my voltages got locked down from Plyndervolt mitigation, I still use it as it lets you adjust the Enhanced Speedstep setting (effects how aggresive the CPU frequency clocks to vs. the load its under, allows you to bias towards lower speeds when on battery to save power or higher speeds to keep the speeds up for games and stuff) as well as change the turbo boost timer duration, allowing more time under boost, as much as you may want until the CPU throttles from thermals. The program was abandoned quite a while ago so it's kind of a toss up on whether it'll work with newer systems, but it's free so you can always try and see.
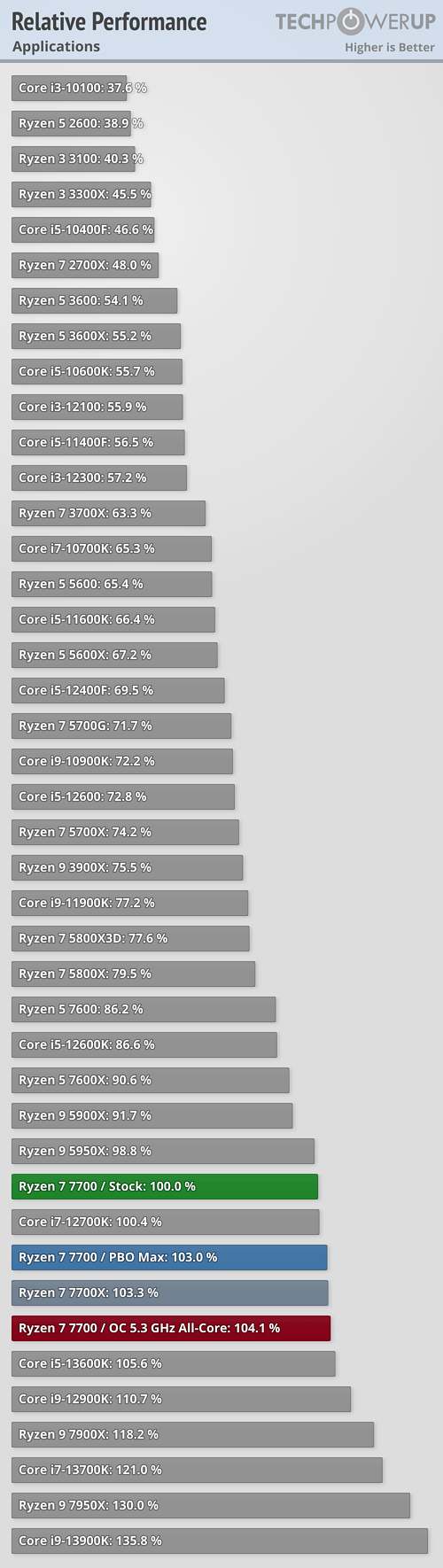
"Microsoft re. cently advised gamers to disable several security features to boost gaming performance. As such, we disabled secure boot, virtualization support, and fTPM/PTT for maximum performance. You can find further hardware details in the, table at the end of the article. "
Not just no, hell no. If you can't strike a balance between security and efficient processing you lean towards security. Gaming is second to not risking your network and integrity. This processor has oodles of power, the impact of security of this basic level should minuscule.
It kinda seems like that sort of thing would be better to look at on a case by case basis. For corporate environments, yes, security, that's a no brainer. I'm not so sure secure boot or TPMs would have too much impact, but I know that with VBS, the memory integrity crap can have a pretty decent impact (although it can be killed without disabling virtualization, but VBS also has other small hits). For someone playing games competively, in twitch response games especially, every bit of performance can make a difference. If that computer is dedicated to gaming then there really isn't data to be taken or lost for real that won't come back with wiping the disks and reinstalls. Pretty much all of that is gonna be saved online. Add some proper network isolation to keep it from talking to other stuff in the LAN and your main network will be reasonably safe. I'm sure I'm over simplifying, but my point is gaming can lead to counterintuitive configuration needs compared to the security-preferential needs of most stuff.