News Tested: Default Windows Setting Slows Games Up to 10%, Even on RTX 4090
Page 2 - Seeking answers? Join the Tom's Hardware community: where nearly two million members share solutions and discuss the latest tech.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
salgado18
Distinguished
Maybe get some of the worst cases and retest them on a mid-range setup, like a Ryzen 5 5800 (or equivalent, even 6-cores will be fine), 16 GB RAM, and a mid-range GPU (RTX 3060 or RX 6600 XT). I'm very curious of the effect it would have, considering you lost up to 10% of the maximum performance of a PC in 2023. Just a few tests to validate if CPU or GPU power is a factor, and by how much.This was me with the 13900K. New test build, totally forgot about VBS. Which is really why this article exists. I freaked out and thought, "OMG how much performance am I losing because of VBS!?" Thankfully, everything was tested on the 13900K with it enabled, so it's still "fair" in that sense. But I'm left trying to decide if I should retest the various GPUs with VBS disabled, or stick with the Microsoft default of having it on? Decisions, decisions...
umeng2002_2
Reputable
It's incredibly irresponsible to promote disabling important security features.
All you need is Common Sense 2023™.
I never really noticed much of a difference in games/ system performance with later mitigations enabled. Mostly just random read performance degradation in crystaldiskmark. The early ones bit though.Keep in mind that if you are truly concerned about gaming/system performance that not only is this mitigation an issue, but you also need to remember Spectre and Meltdown....
Not much of a deal anymore with hardware mitigations having been implemented years ago.
It seems perfectly reasonable if you're a hacker and you want to support these stories being circulated on the internet because you use video games as a doorway into other computers.It's incredibly irresponsible to promote disabling important security features.
Exactly most people will never notice any difference at all because it's beyond the point where it makes a difference. Now if it dropped you from 144 FPS to 60 FPS it would definitely notice it but the drops keep it above 144 substantially. Nothing to see here.I've been running Core Integrity and such on my Intel 10700 for a long while on Windows 11 Pro 64bit install, and honestly i don't notice any performance problems in games i play, and normal daily tasks. i didn't feel comfortable when Windows 11 first launched turning it off then, and don't think i'm gonna these days. As everything seems to be working as normal, games seem fast and responsive, and other tasks do fine as well
It must be nice to have the luxury of being a kid and not having to do bills and banking and stock investing and keeping track of work records and all the other things that people do with their computers and just get to play games. I miss being a kid.If I get a virus, I get a virus. Have never had issues with them even in the days of Windows 98/XP. In the event I get one, I will just do the minor inconvenience of reinstalling windows if I have to (I don't think I have ever really had to do this and I have been pc building since like 2001). At least I will go down doing what I love, which is having my gaming PC perform the absolute best that it can.
Really? So what? How many of those 10 second gains will you need to offset a bricked computer?Turning VBS off in BIOS even sped up my boot time about 10 seconds.
D
Deleted member 14196
Guest
lol I game only on consoles. What, me worry?
this allows me to be a minimalist with a PC which means I don’t spend very much money on hardware or power consumption
I would much rather have a high-end phone than a graphics card even 😆
this allows me to be a minimalist with a PC which means I don’t spend very much money on hardware or power consumption
I would much rather have a high-end phone than a graphics card even 😆
Using what in its place?Ever since windows 10 came out I've disabled defender as one of the first things I do after a clean install.
hotaru.hino
Glorious
I don't really think you understand the scenarios where VBS is actually used. VBS is meant to harden against attacks to grab sensitive data, which for most of us is login credentials and other granted security tokens. It's not for securing whatever saucy data you've been accessing. Programs can still access your files given the user has appropriate permissions.Microsoft VBS entails memory enclaves that block kernel level threats from accessing local data and files when they are loaded into memory. Apple does the same thing with secure enclave.
Turning VBS off is a huge security risk. VBS is a major defense mechanism against the most destructive viruses that gain access to the whole system. VBS blocks these viruses from accessing the OS itself and protects memory and data.
If Microsoft Defender is the front gate protecting your house, VBS is the security guard inside the building . VBS is just as vital as defender to have a secure OS.
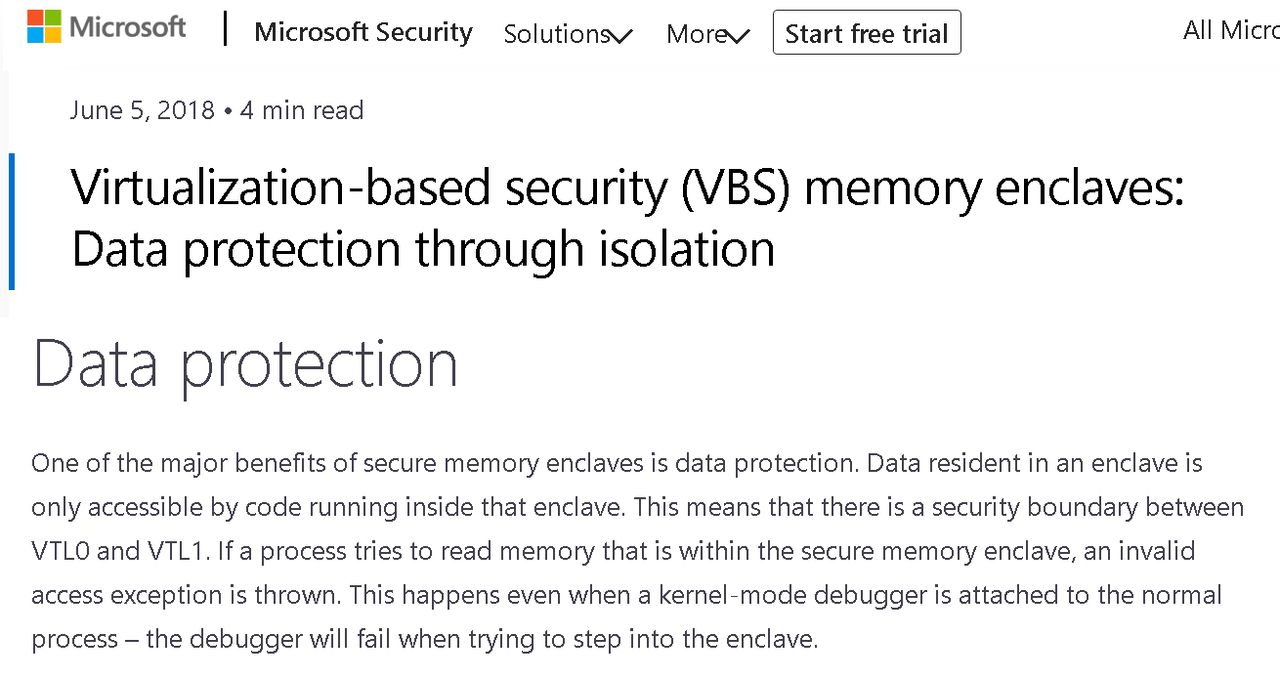
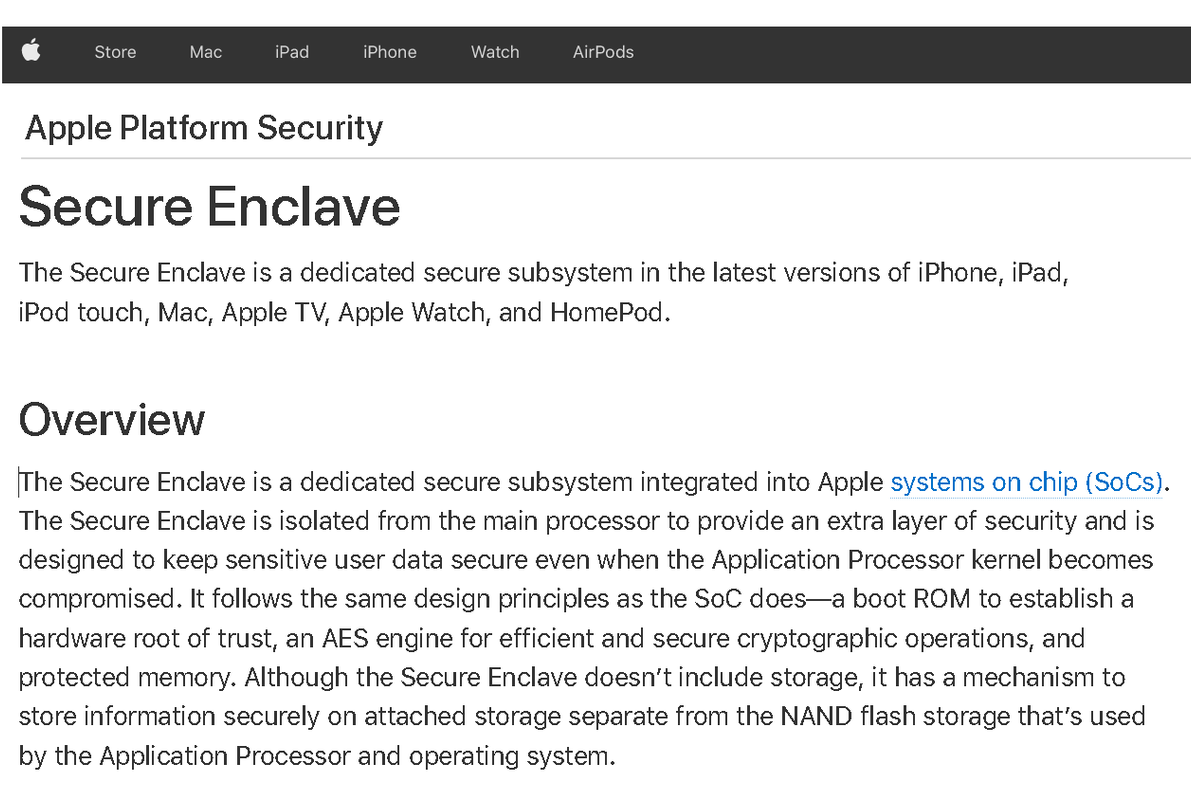
The other aspect of it, only letting signed code run, has been a problem plaguing Microsoft for a long time, and I don't see how VBS does a better job at patching up a glaring loophole in their trusted code system. And even though VBS is supposed to help this, apparently the results are "not working as well as intended" And while this Blackhat presentation on VBS and its issues is over 6 years old, I find it hard to imagine most of these problems were resolved to the point where they're no longer a threat.
To me, all Microsoft did was kick the protection can down the road to Ring -1, rather than implement strategies that are actually more secure. But the point is, while I'm willing to believe VBS offers better protection in some regards, it's not a AT Field that will block all threats.
Also, Apple's Secure Enclave was cracked a while back
EDIT: To note, I would argue that doing what Microsoft, Apple, or really any one is doing with trying to isolate sensitive parts of the OS or computer in their own thing without loss of usability or convenience is really freaking hard.
If you want another example of something else like this that was tried but ended up just being a headache: Intel Software Guard Extensions.
Last edited:
cryoburner
Judicious
I would say to leave it enabled, just because that's the default setting that most people will be using. If you show card A to be running 20% faster than card B in a particular game, but most people will only see it running 15% faster due to them encountering a CPU bottleneck with the default security settings enabled, then that's not really an accurate representation of a card's real-world performance, and could affect a person's buying decisions.But I'm left trying to decide if I should retest the various GPUs with VBS disabled, or stick with the Microsoft default of having it on? Decisions, decisions...
I agree, though I think both a mid-range and older lower-end processor should be tested, to make sure there's enough difference in core counts as well as per-core performance. So, for example, if the high-end CPU was a Ryzen 7950X3D, then the mid-range could be something like a 3600X, and the low-end a 1400, or maybe even a 1200, to help show the maximum effect when a game is starved of processing resources. Or just test the 8-core models from a few generations, disabling cores to roughly simulate the 6 and 4-core options. Testing the performance hit of settings like this on the highest-end hardware may not accurately represent how performance is affected on the more modest hardware that most people are using.Maybe get some of the worst cases and retest them on a mid-range setup, like a Ryzen 5 5800 (or equivalent, even 6-cores will be fine), 16 GB RAM, and a mid-range GPU (RTX 3060 or RX 6600 XT). I'm very curious of the effect it would have, considering you lost up to 10% of the maximum performance of a PC in 2023. Just a few tests to validate if CPU or GPU power is a factor, and by how much.
As for testing with more mid-range graphics cards though, I suspect the differences would become much smaller, or even nonexistent in games where performance becomes mostly graphics-limited.
doughillman
Distinguished
It must be nice to have the luxury of being a kid and not having to do bills and banking and stock investing and keeping track of work records and all the other things that people do with their computers and just get to play games. I miss being a kid.
Hey Chicken Little, you also missed the part where they said they've not had any issues since at least the days of 98/XP. They ain't a kid.
One luxury I have as an adult is the ability to own more than one computer, so I could do all my big boy stuff on one and all my kiddie stuff on another if I was worried about the sky falling. Does that make me more of an adult than you, so I can be pompous? (Seems so, based on the tone of this post.)
casa_is_cool
Commendable
This is a monumentally stupid idea if you do any commerce on your PC.
Ever been hacked? It's a nightmare of time and effort to undo when the fake MSI Afterburner malware tries to spend 2 grand on your credit card.
Ever been hacked? It's a nightmare of time and effort to undo when the fake MSI Afterburner malware tries to spend 2 grand on your credit card.
JarredWaltonGPU
Splendid
You're assuming that VBS alone is responsible for protecting you, and it's absolutely not. If you're already infected by malware because you installed something stupid, I seriously doubt VBS is going to help much if at all. If a website has code that's trying to sniff out data, and your browser allows that, it's a browser problem right at the start, not an OS memory integrity thing.This is a monumentally stupid idea if you do any commerce on your PC.
Ever been hacked? It's a nightmare of time and effort to undo when the fake MSI Afterburner malware tries to spend 2 grand on your credit card.
Bottom line is that when your PC has software running on it that you don't want, but that you accidentally allowed, you're already compromised.
Tac 25
Estimable
my Windows Defender is never turned off. Together with Nod32, they protect my three pc from threats. I use credit card to buy stuff from Japan, so protection is needed.
only Windows function I always have turned off is Background Intelligent Transfer, because it causes lag in some online games I play.
only Windows function I always have turned off is Background Intelligent Transfer, because it causes lag in some online games I play.
This is a monumentally stupid idea if you do any commerce on your PC.
Ever been hacked? It's a nightmare of time and effort to undo when the fake MSI Afterburner malware tries to spend 2 grand on your credit card.
VBS won't do anything for the user installing malware, absolutely nothing.
These technologies are not new, they've been around awhile and about the only thing they really do is prevent a user mode program from accessing sensitive kernel space without going through a trusted OS API first. This isn't supposed to be possible in the first place, but security holes happen and sometimes a driver or other piece of kernel mode code ends up opening an attack vector into the kernel memory space. All this is attempting, to various levels of success, to proactively prevent an insecure driver from being exploitable. Of course this does nothing to protect against a driver that both provides an API and has an exploitable security vulnerability in that API.
Nothing. I don't use any sort of antimalware or antispyware. It slows down the system and deletes legit files sometimes and is just a pain in the arse. False positives are a big problem for me too. And in case you're wondering, I haven't had an infection since widows 10 was released. I don't run shady software and I don't click on any links I'm not sure of.Using what in its place?
Last edited:
Then you're one of the very lucky ones.Nothing. I don't use any sort of antimalware or antispyware. It slows down the system and deletes legit files sometimes and is just a pain in the arse. False positives are a big problem for me too. And in case you're wondering, I haven't had an infection since widows 10 was released. I don't run shady software and I don't click on any links I'm not sure of.
Counterpoint, though...I've never had Defender delete legit files. Ever.
casa_is_cool
Commendable
VBS won't do anything for the user installing malware, absolutely nothing.
These technologies are not new, they've been around awhile and about the only thing they really do is prevent a user mode program from accessing sensitive kernel space without going through a trusted OS API first. This isn't supposed to be possible in the first place, but security holes happen and sometimes a driver or other piece of kernel mode code ends up opening an attack vector into the kernel memory space. All this is attempting, to various levels of success, to proactively prevent an insecure driver from being exploitable. Of course this does nothing to protect against a driver that both provides an API and has an exploitable security vulnerability in that API.
Don't all desktop applications technically use Windows API on Windows 11? confused.
No, API is just an interface into something else, most windows programs are running native and calling API's when they need something outside of themselves. The important distinction is that the programs are running in user mode and by default do not have access into the kernel memory space. But many times programs need to get something from there or otherwise interact with something else inside kernel space, and in that case you would call whatever you needed through some library or interface. But if you knew the kernel space well enough, you could do what you needed to do directly instead, if the OS allows you that is, which it shouldn't (think Windows 98). Of course things exist inside kernel space that often need to communication out, stuff like device drivers or some feature or extension. If one of those items also exposes it's own API or interface, and that interface wasn't secured, then something could attack it and leverage it to gain access into kernel memory.
penguinslovebananas
Commendable
VBS won't do anything for the user installing malware, absolutely nothing.
This right here. For the vast majority of cases the problem does not result from a hacker specifically targeting someone and trying to brute force their system. The majority of malware and information theft is exploiting human behavior and psychology, ie phishing, malware in attachments, etc, and casting a wide net. No security program can prevent this except one where our control is completely forfeited to the program, and I don’t see that being very popular. They best defense you can have is some education, spotting suspicious emailsis a good example and a big part there is identifying the actual email address and not the “name” that is displayed. Also people don’t understand the importance of a backup, NAS units are affordable and easy enough to use now that everyone should have one. People don’t want to invest any effort into things anymore, getting yourself a little knowledge can make a world of difference in many areas.
Tac 25
Estimable
forgot to say. .
I did encounter it a few times.. Windows Defender attack a game installer, thinking it is malware. The solution I did is simply to install the game into Drive F, instead of Drive C - so that WD would leave it alone. This is one reason why I have 12 games in drive F, and only 7 games in Drive C. The other reason for installing in F, is I want Drive C to have as much free space as possible, so most games (espescially the big ones) are in F.
I did encounter it a few times.. Windows Defender attack a game installer, thinking it is malware. The solution I did is simply to install the game into Drive F, instead of Drive C - so that WD would leave it alone. This is one reason why I have 12 games in drive F, and only 7 games in Drive C. The other reason for installing in F, is I want Drive C to have as much free space as possible, so most games (espescially the big ones) are in F.
kerberos_20
Champion
i had ryzen first gen and windows 11 and fps was hammered by around 50% with VBS enabled, which was more than on win10 ~15%, that was while back and ms supposedly improved it a bit, so it doesnt get tanked that hard, but when mbec gets emulated, fps hit is harder than when cpu supports it and yes post is about modern cpus, but older cpus without mbec should note how bad is it to have virtualisation enabledExactly most people will never notice any difference at all because it's beyond the point where it makes a difference. Now if it dropped you from 144 FPS to 60 FPS it would definitely notice it but the drops keep it above 144 substantially. Nothing to see here.
TRENDING THREADS
-
-
AMD Ryzen 9 9950X vs Intel Core Ultra 9 285K Faceoff — it isn't even close
- Started by Admin
- Replies: 47
-
Discussion What's your favourite video game you've been playing?
- Started by amdfangirl
- Replies: 4K
-
Question I have an old system in the basement that has really basic specs, but am planning to give it just a little uplift with an RTX 5060 ti 16gb
- Started by Guy_who_thinks_hes_cool
- Replies: 8
-
-
Question A scared question but I have to ask ?
- Started by Guy_who_thinks_hes_cool
- Replies: 4

Space.com is part of Future plc, an international media group and leading digital publisher. Visit our corporate site.
© Future Publishing Limited Quay House, The Ambury, Bath BA1 1UA. All rights reserved. England and Wales company registration number 2008885.
